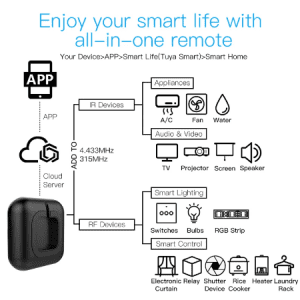
 The Latest version with RF and IR. High compatibility, All-in-one IR and RF remote control. Works with Air conditioning units, TVs, fans, DVDs, STBs, TV Boxes etc. Infrared devices and even RF appliances such as RF lights, switches, RF roller blinds etc. with one single remote control; storage of thousands of IR codes. (Support IR 38KHZ and RF 433/315MHz)
The Latest version with RF and IR. High compatibility, All-in-one IR and RF remote control. Works with Air conditioning units, TVs, fans, DVDs, STBs, TV Boxes etc. Infrared devices and even RF appliances such as RF lights, switches, RF roller blinds etc. with one single remote control; storage of thousands of IR codes. (Support IR 38KHZ and RF 433/315MHz)
Voice Control with Amazon Alexa, Google Home Assistant, Tmall Wizard and others. A simple voice command can activate the controller to remotely control most infrared and RF Devices, such as A/C, FAN, TV, DVD, STB, TV BOX and RF protocol devices.
If you can’t find your branded device in the list of supported devices in the App, then you can manually record the buttons for your controller.
Specifications
Power Input DC 5V/1A (Micro usb2.0)
Model RFIR-R1
Stand-by Power ≤0.4W
Controlling Distance Horizontal direction ≤8m, Opposite Direction ≤15m (Finally effect by environment)
IR control direction Multiple Way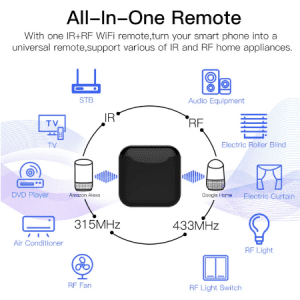
Operating Temperature -10℃~50℃
Operating humidity ≤85%RH
Connection type 2.4GHz 802.11b/g/n
Carrier 38KHZ
APP SUPPORT Android 4.0/iOS 8.0 above
Wireless Frequency 2.4GHz
RF 433/315MHz
Dimension 68*68*27 mm
Note This product supports 315, 433 standard frequency RF, does not apply to 2.4G, Bluetooth, 315 and 433 offset and scroll code devices, self-powered devices.